Stealer Logs: An in-depth analysis of over half a billion stolen credentials
Key Findings
- We analyzed over 590 million credentials from more than 20 million unique infected computers worldwide.
- Brazil is one of the most affected countries by Info Stealers globally.
- Brazil was the most affected country by stealers in 2022 and 2023, and it holds the second position in 2024, slightly behind India in the total number of infections.
- The "Lumma" stealer family has become extremely popular in recent months, reaching a record number of infections in September 2024.
- Credentials exposure through Info Stealers is likely to continue growing, as it has over the past three years. This continuous increase reflects the advancement and severity of these threats.
Introduction
With impressive and uncontrolled growth, malware known as Info Stealers has provided the cybercrime world with a powerful tool: a username, a password, and its cookies. Often, this information alone is enough to cause millions in losses to a company through fraud facilitated by stolen credentials.
Info Stealers are malicious software primarily designed to steal all credentials stored in the victim’s browser, whether they are for streaming services, social networks, banks, or corporate platforms. All this information is stolen and sent to servers controlled by criminals, who compile and resell the credentials to interested third parties.
In addition to credentials, many other types of information are also stolen, such as full computer specifications, cookies, browsing history, files and documents, sessions from applications like Steam and Spotify, cryptocurrency wallets, among others.
In this article, we will analyze data stolen from over 20 million computers infected by Info Stealers malware worldwide. We will explore several interesting aspects revealed by this analysis, including the rise and fall of different stealer families, geographic trends and patterns, relevant events, as well as theories that explain certain behaviors.
This presentation showcases work conducted over years of data collection, processing, and analysis. All the statistics presented have been carefully reviewed to ensure reliable information, as close to reality as possible.
And, of course, given the impossibility of collecting all data related to Stealer infections, all statistics shown are based solely on the data collected and processed by the QuimeraX team. As such, they represent approximations of the global landscape, offering a significant, though not 100% precise, view of the issue.
Currently, the work that enabled this research is directly integrated into the QuimeraX solution, through which we detect, analyze, and report relevant threats, such as those related to stealers. At the end of this article, we will discuss a bit more the role of QuimeraX in combating leaks caused by Info Stealers.
The goal of this article is not to analyze the technical capabilities and methods used by these malware, but rather to examine the data they collect. By doing so, we will explore a different perspective on this contemporary problem and gain new insights into what can be considered one of the greatest security threats today.
The number of exposed credentials has increased considerably
Our analysis is based on the 25,113 files processed up to October 15, 2024, totaling just over 31 terabytes of data. These files, known as "Stealer Logs," are mostly compressed directories; each directory contains the data stolen from a single computer, such as browser passwords, cookies, specifications, and more.
One of the biggest challenges of this research was maintaining the consistency and reliability of the analyzed data. The more than 31 terabytes of collected data do not follow a single format. Each stealer family provides the stolen data in different ways, making the analysis quite complex. However, we were able to achieve a high level of reliability in the information that will be presented.
As of the date of this analysis, the number of unique IPs from infected computers stands at 9,326,964. While the number of IPs is a consistent metric for estimating the total number of infected computers, among other statistics, it is important to note that not all stealer families collect this data. Additionally, networks with dynamic IPs and CGNAT may not be accurately accounted for.
By considering other information, such as username, hardware ID, and hostname, we estimate that approximately 20 million unique computers were infected from 2019 until the date of this analysis (October 15, 2024). This figure aligns with estimates from other sources, which suggest similar results.
However, to ensure concise metrics, we will use only unique IPs as the basis for all further statistics related to infected computers throughout this research.
The graph below shows the count of infected computers from 2019 to the present, broken down by year.
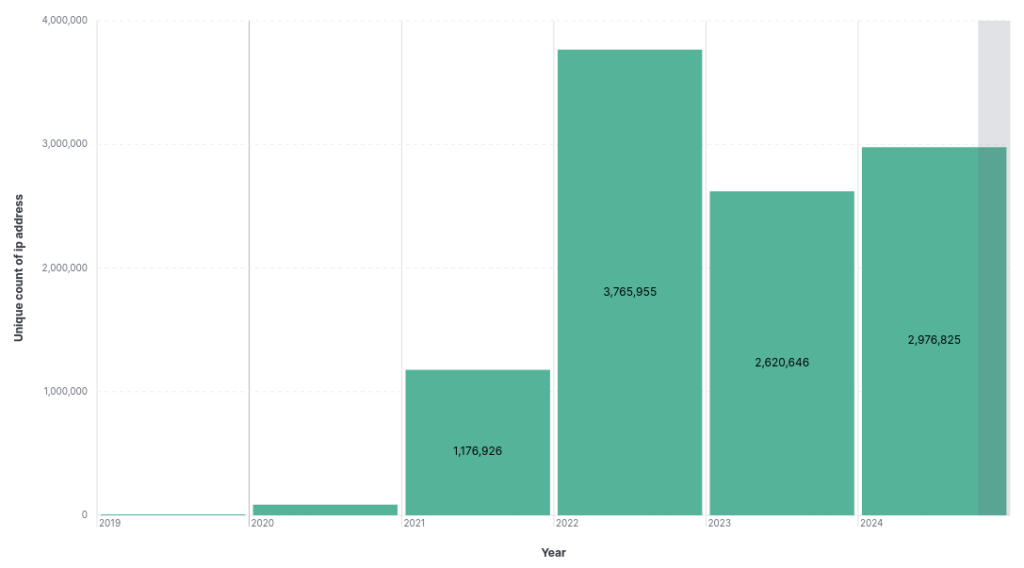
In 2022, at least 3,765,955 computers were infected, making it the record year to date, according to the unique IP count. We observed that in 2023, this number dropped to 2,620,161. However, if we consider the number of unique credentials leaked in the same year, we will find that, in reality, this number exceeds that of 2022.
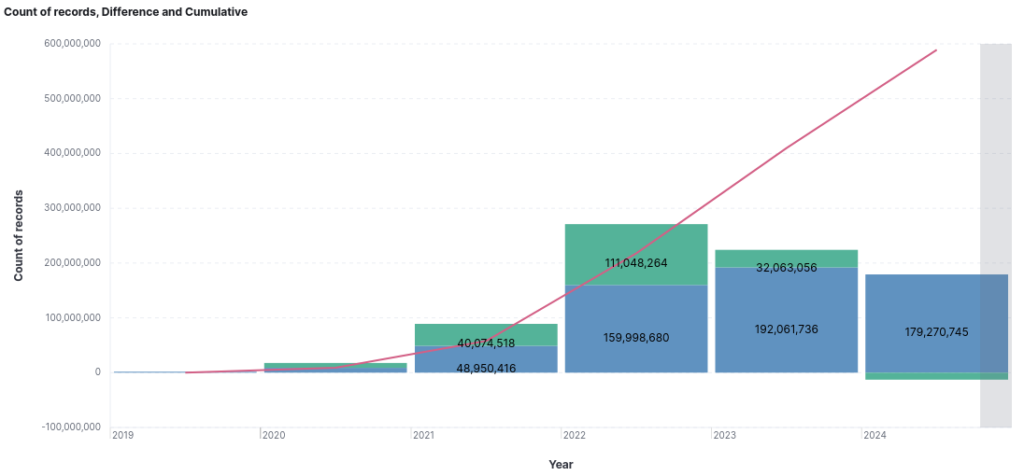
The blue bars represent the total count of exposed credentials for each respective year, while the green bars indicate the variation compared to the previous year. The red line corresponds to the cumulative total of all years.
In 2023, there was a theft of 32 million unique credentials more than in the previous year, representing an increase of just over 20%.
So far, the number of leaked credentials in 2024 has not yet surpassed the total for 2023; however, with more than two months remaining in the year, all indications suggest that this year's count will exceed that of the previous year.
When comparing equivalent periods in 2023 and 2024, a significant increase in the number of leaked credentials is observed.
- January 1, 2023, to October 15, 2023: 130,597,500
- January 1, 2024, to October 15, 2024: 179,270,745
This represents an increase of 37.26%.
In 2023, the last three months accounted for 37.6% of the total credentials leaked throughout the year.
It is important to emphasize that it is through these credentials that criminals gain unrestricted access to various systems, whether governmental, corporate, or banking.
Brazil is one of the countries most affected by Stealers in the world
From 2019 until the cut-off date of this research, Brazil stands out as the most affected country by Stealers in terms of unique IP counts, with 693486 infections, even surpassing India, which has 658594 infections to date.
Below is a table showing the infection counts for the 10 most affected countries.
| Country | Count of infections (Unique Ips) |
| Brazil | 693486 |
| India | 658594 |
| Egypt | 409322 |
| Indonesia | 402086 |
| United States | 312514 |
| Turkey | 308137 |
| vietnam | 284503 |
| Thailand | 250022 |
| Pakistan | 245653 |
| Mexico | 237590 |
When plotting a scatter graph comparing the Human Development Index (HDI) and the number of infections per 1,000 inhabitants, a possible correlation between these two datasets appears.
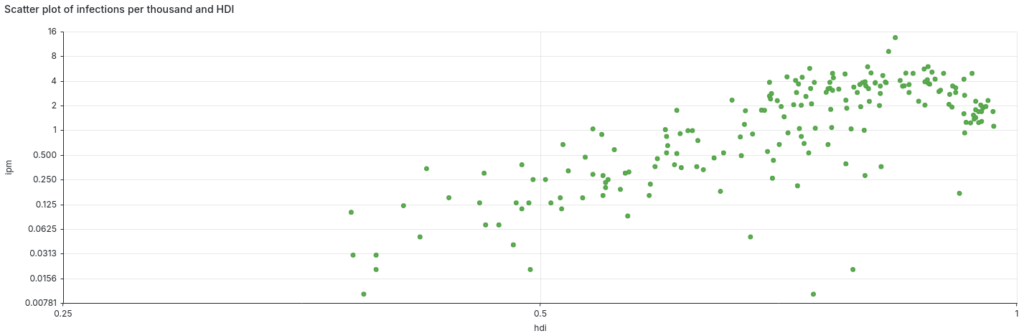
According to the graph, the number of infections per thousand inhabitants shows a positive linear relationship with the Human Development Index (HDI) up to approximately a value of 0.86. Beyond this point, a slight negative linear relationship is observed, extending to countries with the highest Human Development Index scores.
One possible reason for this trend is that more developed countries have greater access to technology, such as computers. Consequently, the greater the access to technological devices, the higher the exposure to stealers and other digital threats.
In absolute terms, Brazil ranks 49th on the list of countries most affected by Stealer infections per 1,000 inhabitants. When considering only countries with populations over 1 million, Brazil rises to 37th place.
Although Brazil is not among the top countries in infections per thousand inhabitants, it stands out in absolute numbers, reflecting both its large population size and factors such as digital access and the prevalence of piracy, which is a common vector for malware installation.
To provide a more visual and comprehensive illustration of the geographical distribution of infections, we present a heat map, in which the most affected countries are highlighted in red.
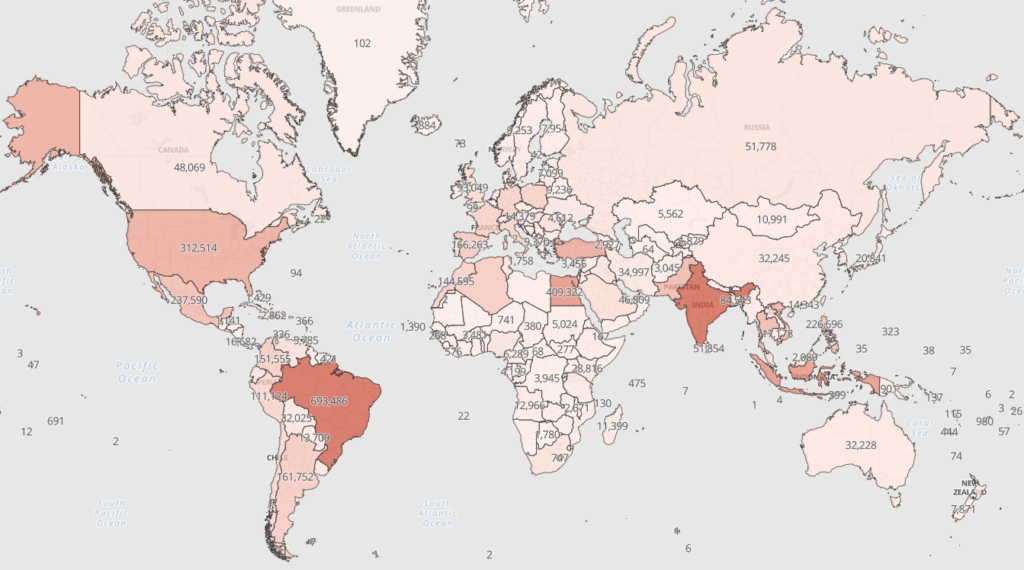
As illustrated in the map, the most severely affected areas include Brazil, India, the United States, and parts of Latin America and Asia. Brazil is clearly one of the global epicenters of this threat. Meanwhile, India also appears as a region with a high concentration of attacks, reflecting the pattern observed in countries with large populations undergoing rapid digitalization.
When considering the number of infections per year in each country, we see that Brazil ranks among the top three most affected countries throughout the entire period analyzed, taking first place in 2022 and 2023.
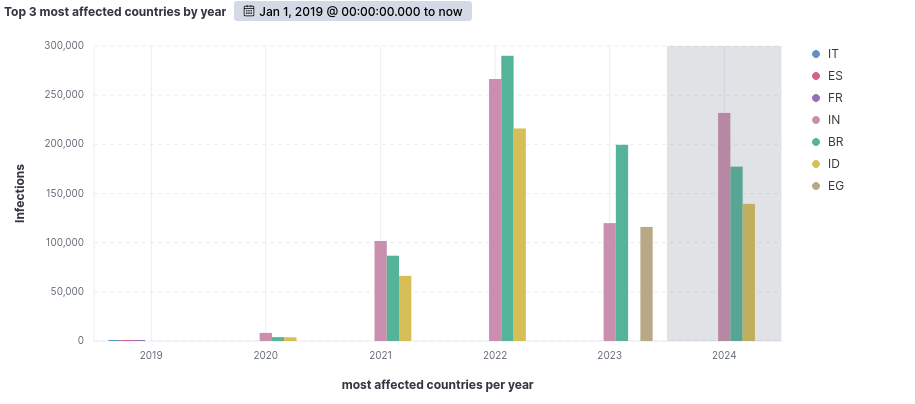
In the current year, however, Brazil is currently in second place in terms of direct count.
Some stealers prevail while others decline
To date, the most prevalent family of stealers affecting computers is "Redline," which is responsible for infecting over 5 million machines and holds the first position with 43% of total infections. Following closely are "Risepro," "Metastealer," and "Stealc," with shares of 11.25%, 10.97%, and 10.96%, respectively.
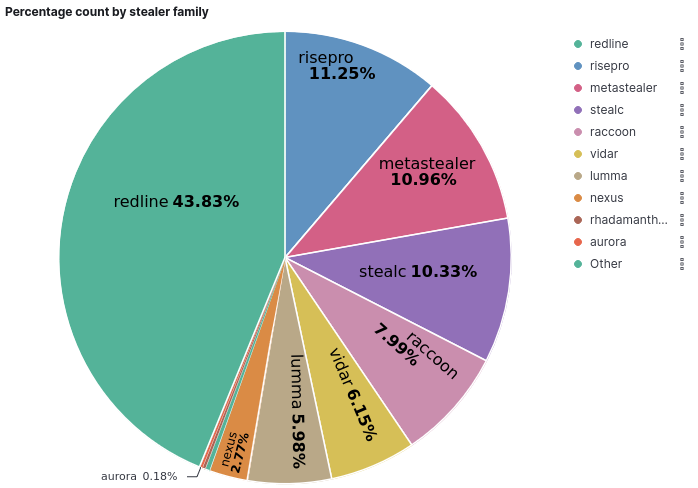
It is observed that the total sum of infections by Stealers family differs from the count of infections by unique IPs presented earlier. This discrepancy occurs because the same IP may have been infected by more than one family of stealers, resulting in an accumulated count. Furthermore, the presence of dynamic IPs and the use of CGNAT, as previously described, also contribute to this difference in counting.
Now, let's analyze the same graph limited to the year 2024, for a more detailed view of the stealer infections that have occurred so far this year.
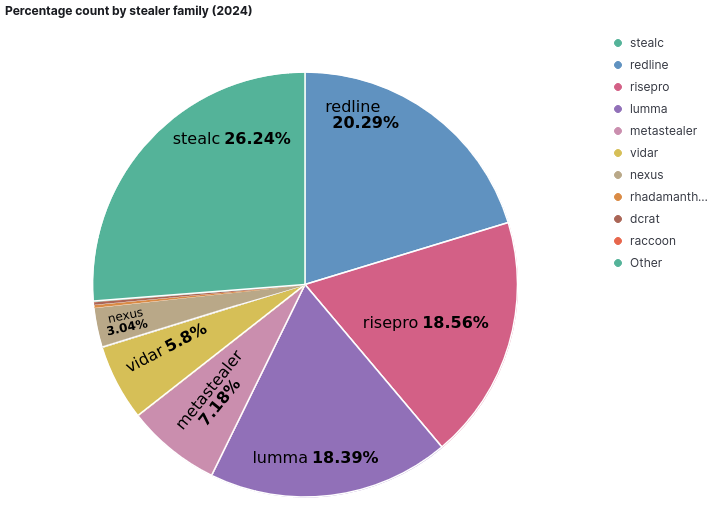
With 26.24%, the stealer family "StealC" holds the first position in the number of infections in 2024, followed by "Redline," with 20.29%. It is noteworthy that some stealer families have lost relevance while others have emerged throughout the current year, compared to the total period analyzed.
When comparing the percentage of infections per Stealers family in each year, the following graph illustrates these variations.
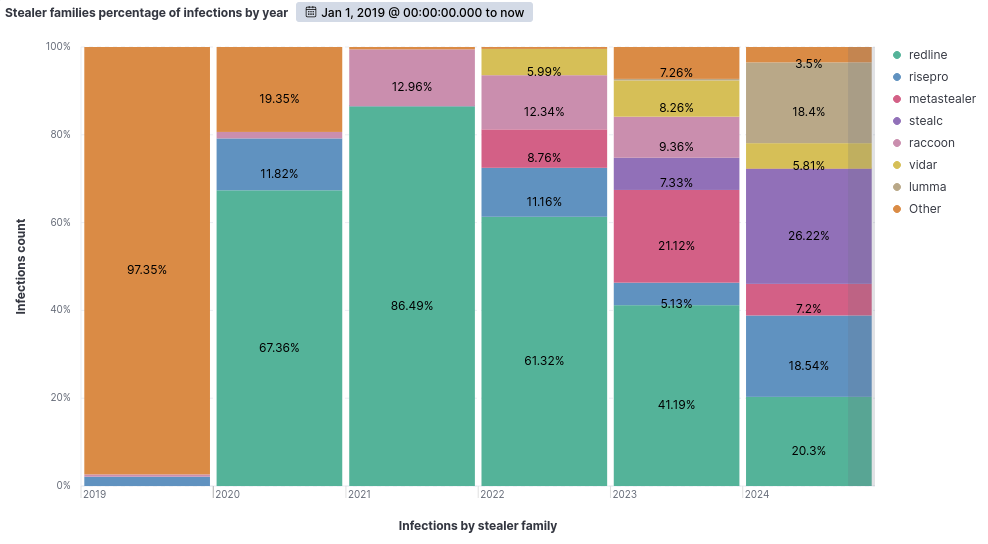
The stealer family “Raccoon” accounts for 0.03% of the total infections this year, in contrast to approximately 12% recorded in 2022.
Similarly, we observe some families gaining traction, such as “Lumma,” which represents 18.4% of the total infections this year, while in 2023, it accounted for only 0.34%.
Additionally, since 2021, we have noticed that “Redline” has been losing ground to other families starting from 2022.
In the following graph, we have a timeline view of the infections of the 8 most prevalent stealers from 2021 to 2024.
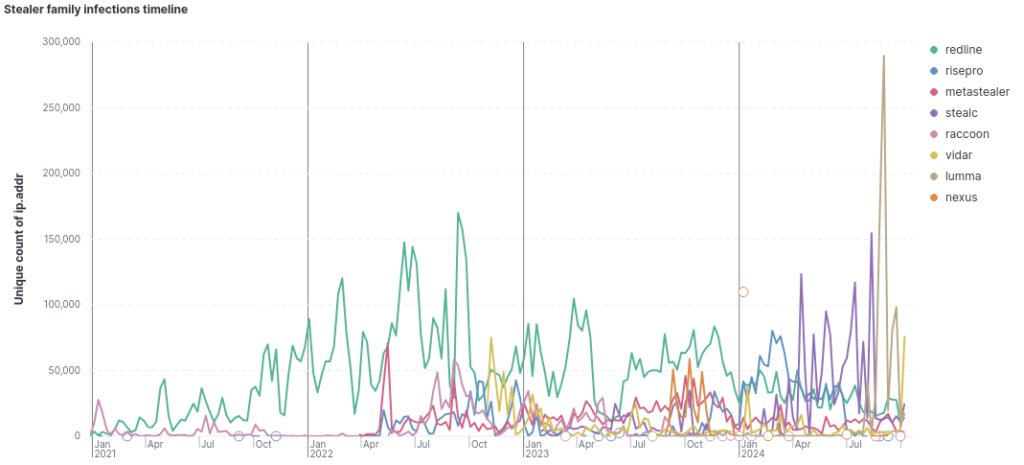
Let's analyze some key points from the graph above:
Between October 2021 and October 2022, "Redline" stood out as the most prevalent stealer, with an average of just over 226,000 infections per month. However, this average dropped to 118,000 infections per month in the following year.
After the first half of 2023, the "Raccoon" stealer virtually ceased to exist, with just over 35,000 infections recorded after that date.
“Risepro” and “Metastealer” followed opposite trajectories at similar times. From April 2022 to January 2023, both stealers exhibited similar prevalence rates. However, from February to October of the following year, “Metastealer” significantly surpassed “Risepro,” achieving an average of 57,000 infections per month compared to 4,400 for Risepro.
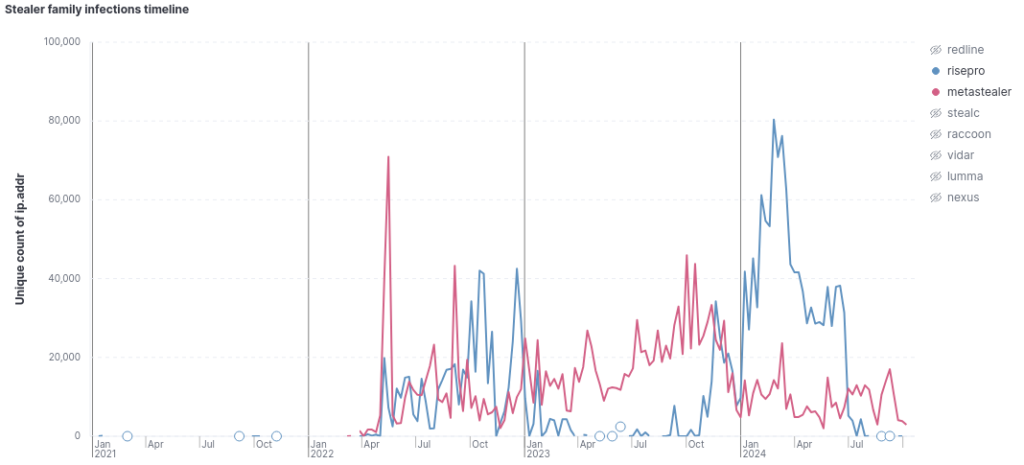
“StealC” leads in the number of infections in 2024, while Lumma sets a record for infections in September.
The month of September over the past three years has stood out in comparison to adjacent months regarding the number of leaked credentials, for reasons that are not yet fully understood. The graph below, illustrating the number of leaked credentials per month during this period, highlights this phenomenon.
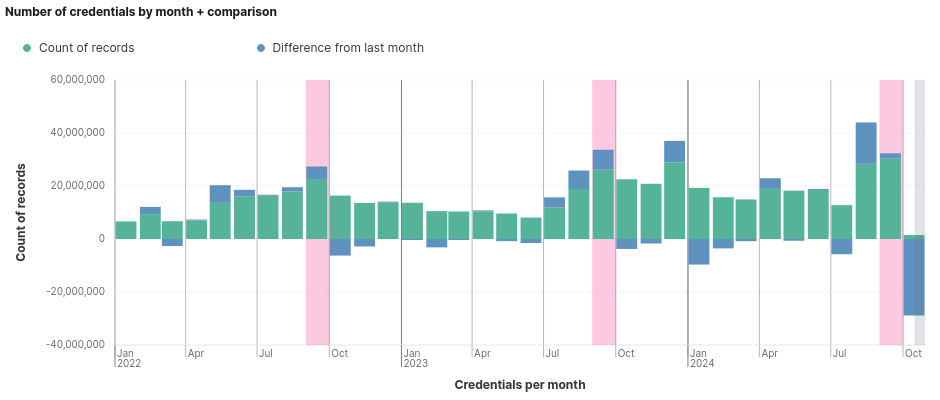
This year, in September, there was a leak of 2,176,797 more credentials compared to the previous month. In 2023, this number was even more significant, with an increase of 7,402,256 leaked credentials.
Additionally, September 2024 recorded a record number of infections from the stealer "Lumma," marking the highest number of computers infected by a stealer in a single month to date, as shown in the following graph.
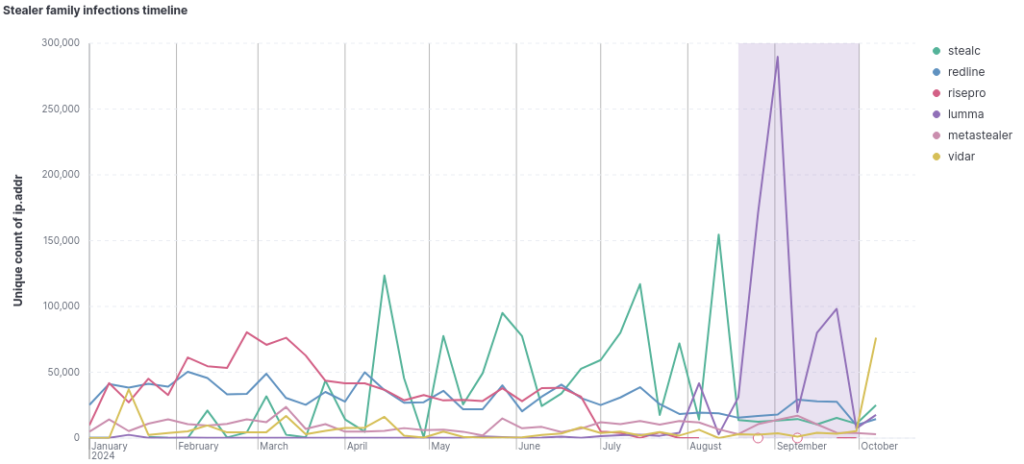
It is also important to highlight the recent spike in infections caused by the stealer "Vidar" in the past week. Throughout the year, this family of stealers maintained a consistently low number of infections, but it has now reached a new record in its activity.
This kind of information is crucial for understanding emerging trends and current risks related to digital security.
Conclusion
In light of all that has been presented, we can conclude that stealers are here to stay and are becoming an increasingly critical issue. We have observed that both the number of leaked credentials over the months and the number of variants of this type of malware have been continuously increasing.
The aim of this research was to shed light on statistics that are rarely presented to the public, with the intention of highlighting a problem that, perhaps, many are still unaware of.
Many of today's major security incidents are caused by info stealers. Perhaps one of the most critical examples is the data breach at TicketMaster, where the attacker used an exposed credential from stealers to gain access to the database containing customer information. The credential in question belonged to a third-party database management service called Snowflake. Upon briefly reviewing this case, we found that an employee of Snowflake with access to the system fell victim to a stealer on September 19, 2023. Seven months after this incident, the APT group known as "Shiny Hunters" publicly announced the sale of data from 560 million TicketMaster customers.
Certainly, some details were omitted from this research due to the impossibility of exhaustively analyzing all the information in a single text without making it excessively lengthy and tedious. However, several key points, characteristics, and peculiarities will be explored in future research.
There are numerous ways to prevent info stealers. Security education and the adoption of preventive measures are fundamental, but implementing monitoring mechanisms is an essential practice for staying informed about potential incidents caused by info stealers.
QuimeraX is an EASM (External Attack Surface Management) and Cyber Threat Intelligence solution that provides this type of monitoring, along with many other functionalities. All the data presented in this research is used to monitor, predict, and mitigate real threats.To learn more about QuimeraX, visit quimerax.com and schedule a DEMO with us.
References
HID Dataset
https://hdr.undp.org/data-center/human-development-index#/indicies/HDI
