[EN] The Brazilian cybercrime community is now building a nationwide Facial Recognition System
![[EN] The Brazilian cybercrime community is now building a nationwide Facial Recognition System](/content/images/size/w1200/2025/08/2025-08-04_11-46.png)
Introduction
Brazil has faced problems related to the privacy of its citizens’ data for many years. The decentralized nature of government systems, the lack of strict security protocols, and the neglect of regular audits create the ideal environment for exploiting vulnerabilities and stealing information from different government entities.
Looking back, around 2015, the "hacker" community at the time (made up of amateurs, enthusiasts, and students) discovered a new way to search for personal information of any individual with a national taxpayer registry in Brazil. A single system, called CADSUS (Cadastro do Sistema Único de Saúde), allowed healthcare professionals to search for patient information nationwide.
Ten years after this event, the current “hacker” community (now composed of fraudsters, organized criminals, and scammers) has created a system that, starting from a person’s facial photo, makes it possible to discover all their other personal information: vehicles registered in their name, driver’s license data, addresses, phone numbers, emails, relatives, debts, social and economic class, job, and registered companies.
Today, we will explore the newest and boldest undertaking of cybercrime: a facial recognition system that affects millions of people in several Brazilian states and that, very soon, will most likely be used throughout the entire national territory.
Query panels have evolved in recent years
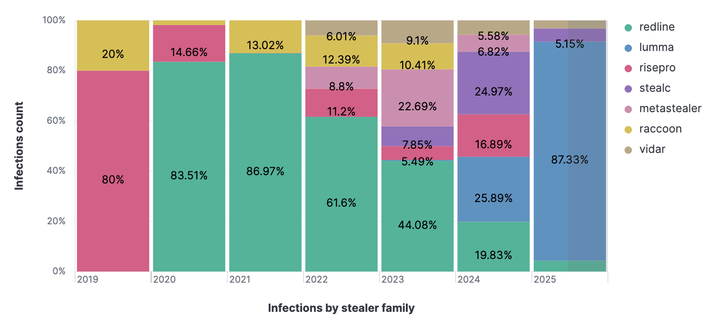
A “painel de consulta” (query panel), as it is known in Brazil, is essentially a website where it is possible to search for the personal information of any individual. Access to these systems is usually sold through a monthly subscription that typically ranges from R$100 to R$300. The system offers access to various “modules”, each with a specific purpose. These modules are used to perform different types of searches. In most panels, there are modules for checking vehicles linked to a CPF, addresses associated with a CPF, complete basic data, debts in the person’s name, government benefits, and many others.
These “query panels” have existed for quite some time and are always similar to each other. Their main function is to provide a wide catalog of data lookup options, meeting the demand of those who want information about third parties. To achieve this, the query panels integrated with external systems to perform on-demand searches for their users. It was not uncommon, for example, to find a module called “CADSUS Query” — that is, a module that searched for information in the SUS database through access to the CADSUS system.
Over time, various systems were discovered and increasingly made available for querying through these panels. Among them were systems querying the databases of the Federal Revenue, the Detran (vehicles and people), state police databases, as well as legitimate information and credit-checking companies such as Serasa, SPC, Boa Vista SCPC, and many others.
The main problem faced by the operators of these panels was obtaining credentials to access the external consultation systems. However, at the end of 2021, a new wave began to emerge — something that would revolutionize these systems: infostealers.

Query panels started to maintain their own databases instead of using external systems
The credentials stolen by infostealer malware granted access to countless systems that had not yet been explored by cybercriminals. Suddenly, modules began to appear for querying arrest warrants, police reports, incident records, legal proceedings, digital vehicle registration (CRLV-e), and even photo and fingerprint data of individuals. Even though the federal government made some efforts to centralize information and improve its overall security, cybercrime was faster and gained access to hundreds of these decentralized systems that contained extremely sensitive information.
However, over time, the systems evolved and became increasingly difficult to access. Some implemented MFA, while others restricted access through VPN. These efforts were made to contain the power of infostealers, which had given criminals an unprecedented weapon: a large number of credentials at extremely low prices.
With these new obstacles, cybercriminals moved ahead and began extracting data from systems that previously operated solely on an “on-demand” model. Downloading and storing the data locally would extend the lifespan of the query panels, since they would no longer need to constantly look for new systems or wait for new credentials to be stolen. In addition, competition for those credentials was becoming increasingly intense, as they were also becoming easier to obtain.
As a result, countless data brokers also began to emerge. Just as they had previously sold CADSUS access credentials, they started selling the databases themselves in CSV files — with no expiration date, no need for credentials, and the ability to explore the information in a much more in-depth way. This is how the market for selling databases began in Brazilian cybercrime. Now, many of the databases from systems used for queries have been extracted and later commercialized to countless individuals.
A new era for "query panels"
On July 2nd, at 11 PM, a relatively well-known query panel announced a new consultation module: facial recognition for different states.

The message announced the creation of facial recognition modules for at least nine Brazilian states. The combined population of these states is approximately 101,589,747 people, according to 2024 estimates.
By accessing the panel, it is possible to explore various standard query modules, such as CPF data, vehicle license plates, driver’s licenses, legal proceedings, and photos.
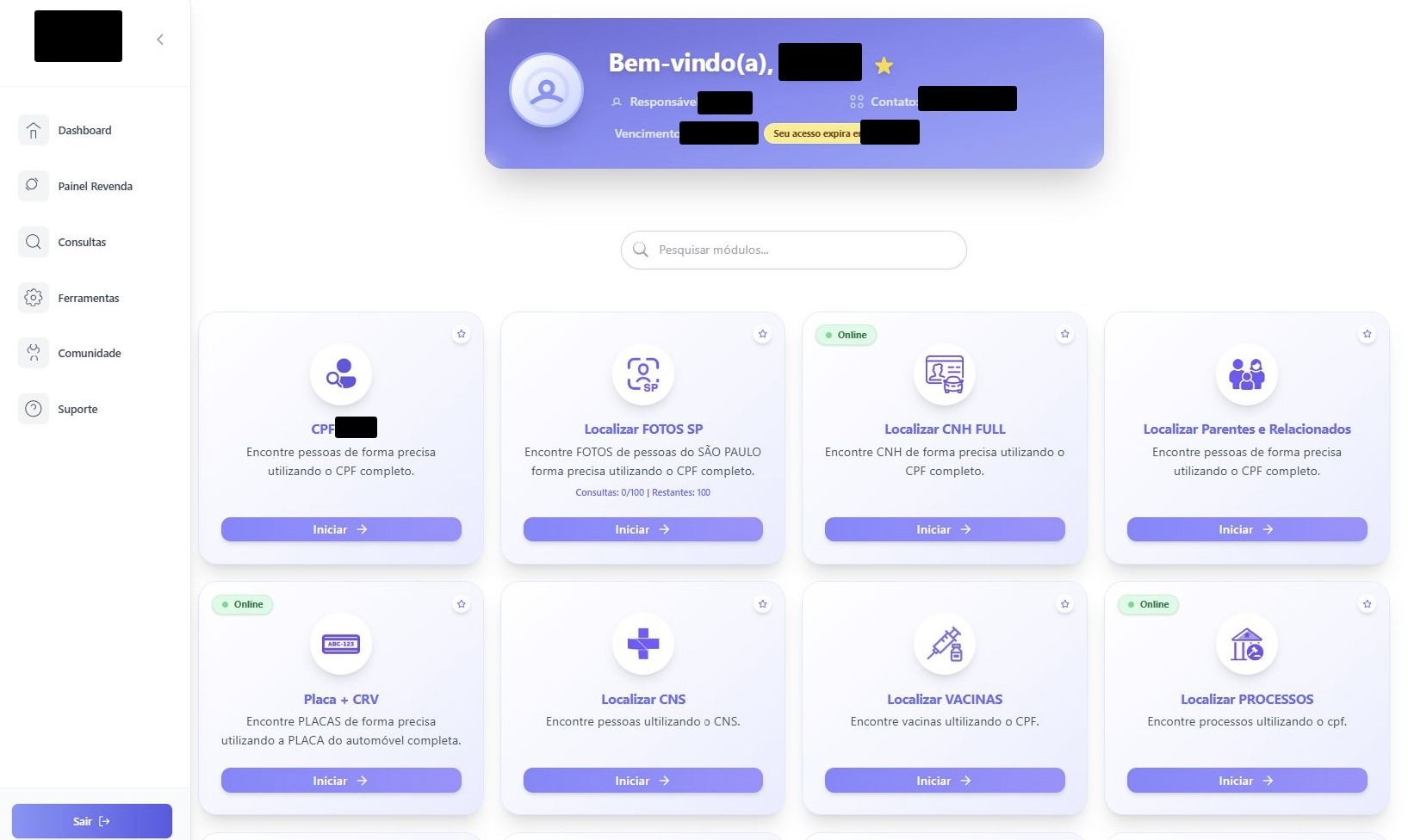
However, in addition to what is typically expected in a query panel, some facial recognition modules are also available.
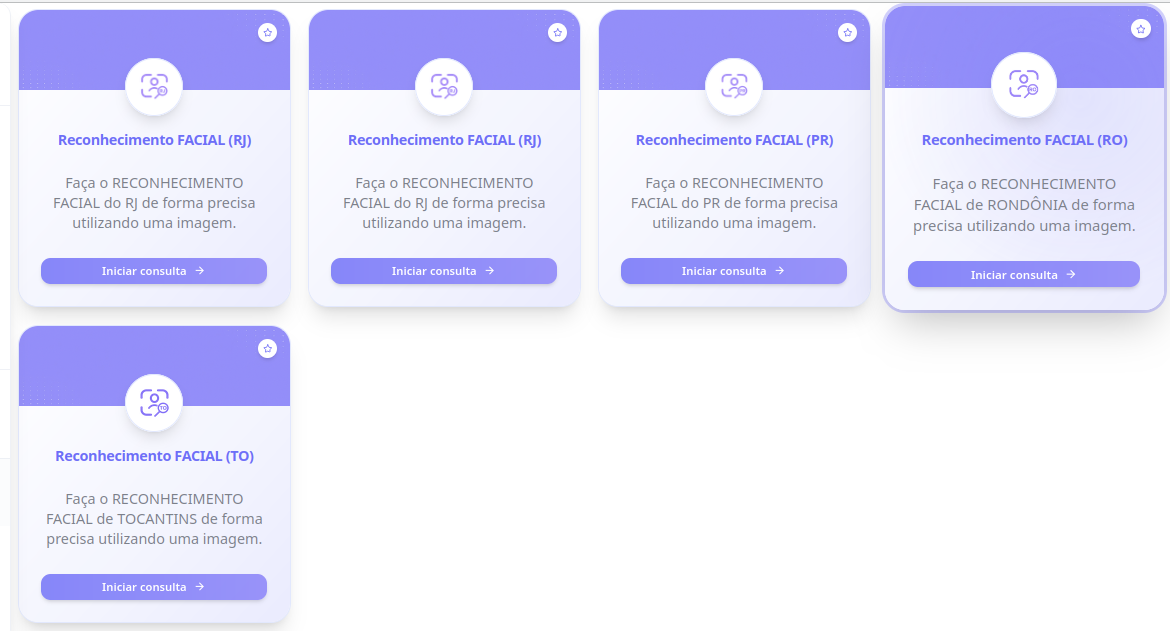
Upon entering the RJ module, there is an option to upload a photo.
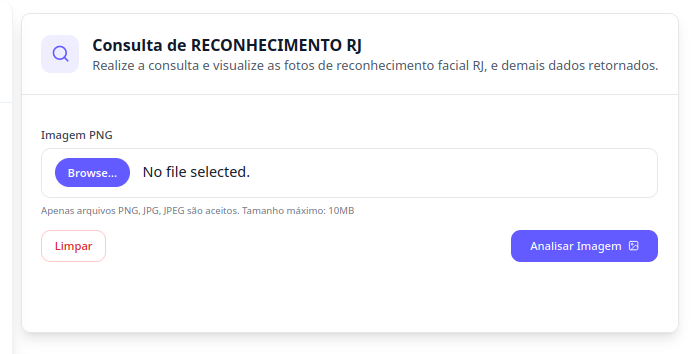
To test the module’s functionality, we obtained a photo of a random person from the Rio de Janeiro state wanted persons website (all sensitive data has been redacted).
Upon uploading the photo, the system warns that the search results may take between 2 and 5 minutes.
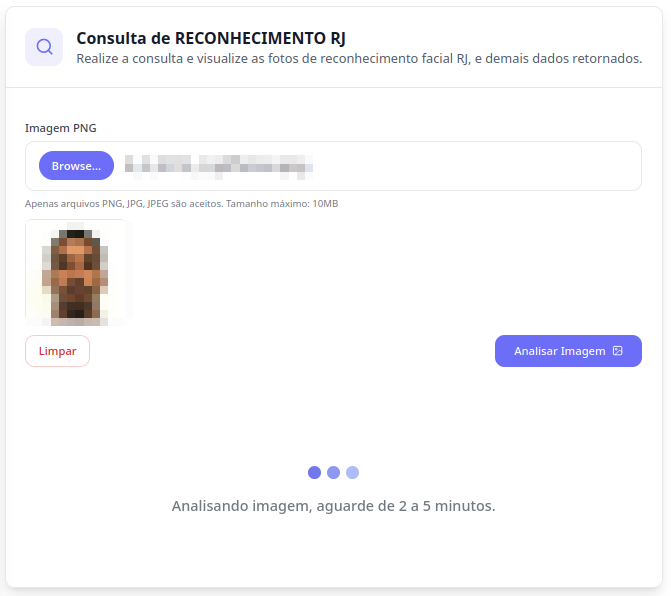
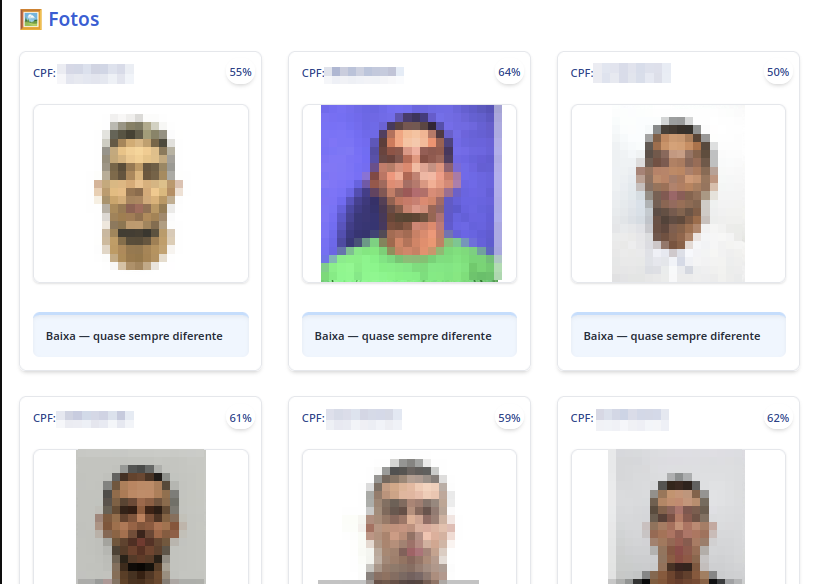
After this period, the system returns a list of possible names, along with their respective CPFs and photos for comparison. In this specific case, the system was unable to identify the person in the uploaded photo.
In a new test, we used the photo of the second person returned to perform another search in the system. This time, the system accurately returned the consulted person’s information with a high level of reliability, according to the system itself.
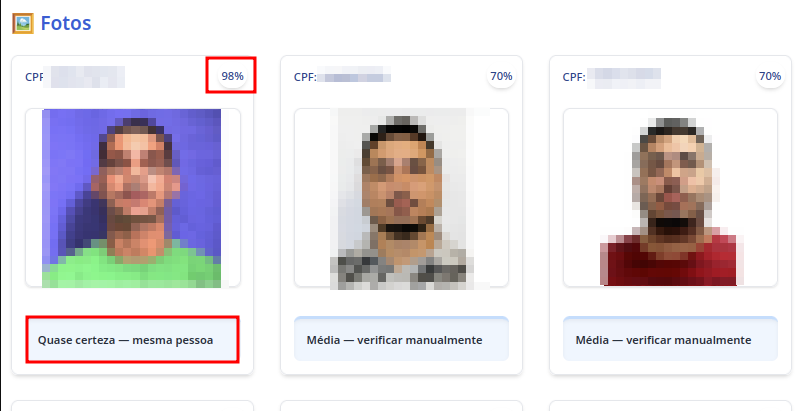
Indeed, it can be said that the system is still somewhat imprecise and requires improvements to become more robust and deliver better results. However, the mere existence of this system already represents a significant threat to public security. Ten years ago, query panels only included simple modules for CPF or vehicle license plates; today, however, with just a facial photo, it is possible to potentially obtain all of a person’s data.
In a world where all banks and other financial institutions adopt at least one biometric authentication factor, fraud involving biometrics is highly sought after by criminals. Gaining access to a database of facial photos of millions of people, identified by their CPF (national unique ID), represents an unprecedented risk, never before faced by banks or fraud prevention institutions.
How is large-scale facial recognition performed?
Out of curiosity, let’s briefly explore how facial recognition is carried out from an image.
The basic logic of large-scale facial recognition involves extracting unique parameters from faces (called face embeddings), storing these parameters in a vector database, and then searching for the parameters that are closest to another face.
The process can be divided into five main steps:
- Face Detection: the model detects and isolates the faces.
- Alignment: the detected face is standardized (normalized) in terms of rotation, scale, and position, usually using key points such as the eyes, nose, and mouth.
- Parameter Extraction: the model transforms the face image into a multidimensional numerical vector representing facial features.
- Database Insertion: the extracted vectors are stored in a vector database, such as Qdrant.
- Search for Similar Faces: after extracting the parameters of the face to be searched, the vectors are compared with those in the database using distance metrics (such as cosine or Euclidean). If the person has been previously registered, the closest result should be the individual being searched for.
This article on the Elasticsearch blog, a non-relational database, presents this methodology in more detail: How to Build a Facial Recognition System Using Elasticsearch and Python.
What we can observe is that there is no need for large processing power or storage to perform these operations; it is only necessary to gain access to an identified biometric database, extract the face parameters, and store them in a specialized database.
Conclusion
This case is just one among many incidents involving data leaks in Brazil. No other country is known to provide such widespread access to its citizens’ information, cheaply and easily, to anyone wishing to acquire it for various purposes.
The centralization and security efforts of the federal and state governments have not been fast or efficient enough to prevent thousands of people from gaining unauthorized access to citizens’ highly sensitive data.
Anti-fraud and biometric verification companies must be aware of their adversaries’ capabilities, monitor their activities, understand emerging trends, and anticipate future risks.
Want to stay up to date on intelligence, data, and the main cybercrime risks? At QuimeraX, you’ll find exclusive reports with monthly analyses that reveal trends, emerging threats, and strategic information to protect your company. Access: https://lp.quimerax.com
QuimeraX monitors daily activity in major Brazilian and international cybercrime communities. We anticipate threats, produce continuous reports, and maintain ongoing communication with our clients across various sectors. We understand existing vulnerabilities and how fraudsters exploit them to carry out illicit operations.
The platform’s major differentiator is applied intelligence: clients do not receive an overload of irrelevant alerts, but rather filtered, contextualized, and truly critical information. This ensures visibility, rapid response, and the prevention of attacks such as fraud, ransomware, and corporate credential compromise.
Request a free demonstration and see Quimera in action! Access: https://quimerax.com/

![[PT] From Data Leak to Intelligence: Analyzing the C&M Software Exposure](/content/images/size/w720/2025/12/image-9.png)
![[PT] The Brazilian cybercrime community is now building a nationwide Facial Recognition System](/content/images/size/w720/2025/08/2025-08-04_11-46.png)